Ransomware as a Service Attack on the NGO Water for People!
It is believed that no one would ever refuse to give a drink to someone thirsty.
However, the world of crime is a completely different world that doesn’t abide by the rules and doesn’t value collective ethics.
This means that cybercriminals, who are not kind-hearted at all, can target anyone without remorse, even non-profit organizations that provide vital goods and services to people around the world.
Recently, Water for People, a non-governmental organization (NGO) established in the early 1990s by the American Water Works Association, was hit by a ransomware attack.
The organization was created in response to growing water shortages in developing countries and currently operates in 9 countries including Bolivia, Guatemala, Honduras, Peru, India, Malawi, Rwanda, Tanzania, and Uganda. It aims to enhance access to clean water for about 200,000 people in the next 8 years.
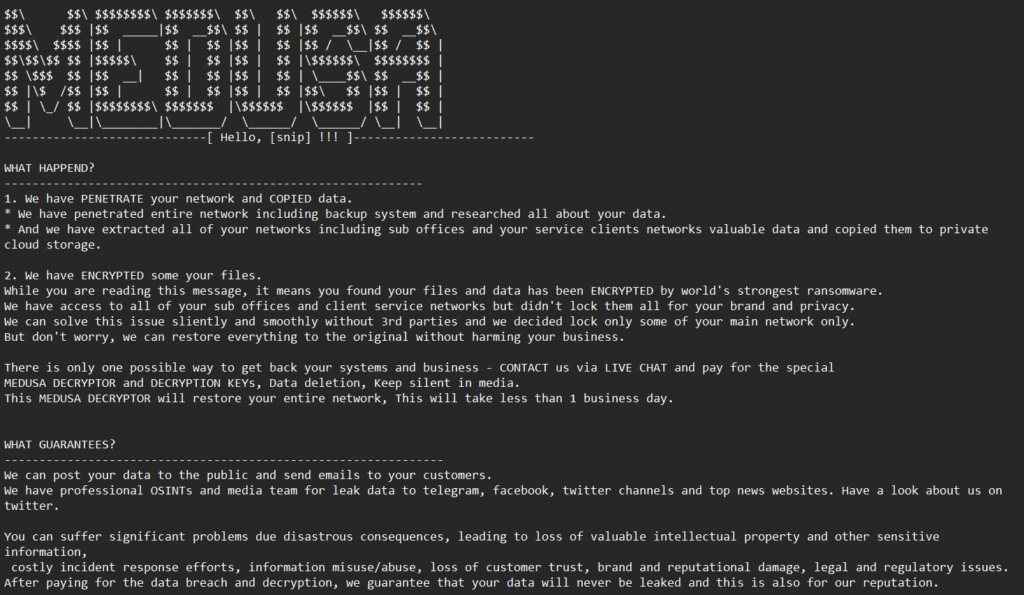
The Medusa gang claimed responsibility for the attack and demanded a ransom payment of $300,000 within 10 days to prevent them from publishing the stolen data and information.
A Water for People spokesperson confirmed that the stolen data
“The recent cyber attack by Medusa Locker Ransomware – he said – did not affect our important work combating the global water crisis and promoting sustainable access to clean water and sanitation”.
Although the NGO is reassuring those concerned, it is
It is worth noting that just before this attack, Water for People had received a $15 million donation from MacKenzie Scott, the billionaire ex-wife of Amazon founder Jeff Bezos. Although there is no evidence that this donation was the reason for the attack, the suspicion is well-founded.
Non-profit organizations are particularly vulnerable to cyber attacks as they collect and store sensitive user data, including donor and volunteer tax codes, credit card data, personal health information, and more.
The Medusa ransomware
The Medusa ransomware, also known as MedusaLocker, was first identified in September 2019. It primarily targets Windows computers and has been responsible for several attacks on various entities, including companies, government bodies, and healthcare providers.
The group behind the Medusa ransomware encrypts the victim’s data, denying access to their devices, and then demands a ransom to unlock them. The threat is usually the publication of sensitive information.
It’s worth noting that not all criminal gangs are the same. Some, like the DarkSide group, have a code of conduct that prevents them from attacking certain organizations, including schools, non-profit organizations, NGOs, and other socially relevant entities.
Ransomware-as-a-service, the new service agencies for criminals
Many experts are convinced that the increasingly widespread use of Ransomware-as-a-service (RaaS) has recently played a key role in keeping the spread of ransomware high; it remains one of the types of attacks most widely used by criminals. A 2022 report by Zscaler found that 8 of the 11 most active ransomware variants were RaaS variants.
The RaaS model has become increasingly popular among cybercriminals because it is also accessible to amateur
On the other hand, developers can earn money without carrying out a direct attack and without getting their hands too dirty. They develop and package their malicious tools, organize them into kits and subscriptions (annual, monthly, one-off) and sell them to other criminals on the dark web.
Often, along with the malicious product, developers sell a number of services: technical support; access to private forums for advice and information shared between hackers; access to portals for payment processing (mostly in cryptocurrencies); advice for personalised writing of ransom requests, or for negotiating with victims.
These are real service agencies for those who want to pursue a career in cybercrime, dangerously expanding the attack surface by onboarding unscrupulous, amateur criminals.
How to defend oneself against Ransomware
“We need to pay more attention to the security of our organizations due to these changes.”
It is important to emphasize that awareness is the first step in protecting oneself from cyberattacks.
Although technological tools can help prevent these attacks, the most effective weapon is providing individuals with proper training and education to develop personalized digital habits.
The human factor remains the main factor that puts security at risk.
Therefore, the key words to bear in mind are awareness, attention, effective training, and education, which should be tailored to individual needs, including the use of artificial intelligence and machine learning.




